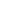Enterprise apps are what keep companies running businesses from employee-facing tools to customer-centric digital experiences. Strong enterprise application security is increasingly critical as complex web and mobile platforms become the norm for expanding organizations. These applications process sensitive data, link to multiple systems, and run for many users, making them attractive targets for cyberattacks.
Organizations are hitting on the following security pain points that impact today’s modern enterprise – from open-source components putting you at risk, to insecure integrations and mobility taking over. Lack of a defined enterprise app security strategy exposes enterprises to data breaches, compliance concerns, and business outages. Developing for the Enterprise. Secure development of enterprise software is about engineering security into our software lifecycle, not just as a final gate.
As more mobile-first offerings and connected enterprise ecosystems enter the market, it’s also important that businesses give serious attention to enterprise mobile app security, as well as security around system integrations. Whether working with an internal team or a trusted Cross Platform App Development Company, organizations must ensure that security standards are consistently applied across web, mobile, and backend systems. A clear enterprise application strategy helps balance protection needs with collaboration, scalability, and long-term sustainability. This guide explains how to develop secure enterprise apps that meet both modern business and security requirements.
Understanding Enterprise App Security Fundamentals
Enterprise app security targets the protection of applications that underpin significant commercial activity, personal data, and intricate business processes. Enterprise applications, unlike consumer apps, interface with many systems, users, and third-party services – which widens their attack surface. Enterprise app security ensures the confidentiality, integrity, and availability of web, mobile, and backend systems.
At its core, enterprise application security involves protecting application code, APIs, backend datastores, user access, and third-party integrations. Typical challenges include weak authentication, insecure access controls, unpatched vulnerabilities in third-party open-source libraries, and misconfigurations of cloud-hosting services. Without a business-grade level of defence, these vulnerabilities can result in a breach or loss of data, financial implications, or regulatory sanctions.
If you build enterprise software, the only way to be secure is to have a proactive security program integrated into your development lifecycle. It should go without saying that the above-mentioned factors include secure coding practices, frequent vulnerability testing, dependency management of open-source components, and ongoing monitoring. These security basics enable businesses to build reliable solutions that can scale and grow, while managing risk effectively
Example:- Imagine it’s an enterprise HR app that includes payroll, attendance, and a mobile employee app. In the case that an obsolete authentication library is utilized, for example, an open-source one, and it is not maintained/patched over time, attackers could exploit its weaknesses to access confidential data. This one weakness could have led to the exposure of employee records, salary information, and internal systems. With secure coding practices, up-to-date dependencies, and strong access controls in place, the organization can avoid these breaches while holding on to its secure enterprise software.
Read More:- Cybersecurity for Outsourced & Remote Software Teams
Enterprise Application Strategy for Security-First Design
A security-first enterprise application strategy puts security into every step of the software development process, rather than trying to tack it on afterward. The following are the steps enterprises should take to ensure their applications are built to be secure, scalable, and resilient.
Key Steps in a Security-First Enterprise Application Strategy
- Define security requirements early
Identify sensitivity of data, compliance requirements, and risk exposure upfront to inform architecture/design decisions.
- Choose a secure enterprise app platform
Choose holders that incorporate security features like encryption, role-based access control, and audit logging.
- Implement centralized identity and access management
Reduce the discrepancy in access between web, mobile, and internal applications by delegating all logic to a single system for authentication and authorization.
- Embed security into the development lifecycle
Employ coding guidelines for secure coding practices, security scanning tools, and follow data privacy standards to ensure the product is safe from security threats; also, maintain zero vulnerabilities throughout development by cross-verifying against national vulnerability databases.
- Enable secure enterprise security and collaboration
Secure all data sharing between teams and systems with secure APIs, encryption, and controlled access policies.
- Continuously monitor and improve security posture
Monitor the state of application security, and evolve security controls to fend off new threats as enterprise essential services change.
By conducting the above, companies can create secure enterprise software that combines innovation and collaboration with enterprise-grade security.
Enterprise Mobile Application Security Best Practices
Enterprise mobile apps are no longer just “nice to have.” They’re how employees check data, approve work, and stay productive when they’re not at a desk. Because these apps handle real business information, enterprise mobile application security has to work quietly in the background—without slowing people down or getting in the way.
What actually works in real-world enterprise mobile security
- Make access simple but strict
Don’t rely on passwords alone. Multi-factor authentication and role-based access make sure the right people get in, even if a device ends up in the wrong hands. - Assume devices will get lost
Phones go missing. It happens. Encrypting data and limiting what’s stored on the device reduces damage when it does. - Treat APIs like front doors, not back doors
Mobile apps constantly talk to enterprise systems. Securing APIs with proper authentication and monitoring prevents silent data leaks. - Don’t ignore open-source shortcuts
Open-source libraries save time—but outdated ones create risk. Regular updates and scans close gaps that attackers often exploit first. - Give IT control without micromanaging users
Mobile app and device management tools help enforce security policies without disrupting daily work. - Keep checking, even after launch
Security isn’t “done” once the app is live. Continuous testing and monitoring catch problems before users or attackers do.
When these practices are followed consistently, enterprises can support flexible work and mobile productivity while maintaining strong enterprise app security—without making security feel like a burden.
Read More:- Why Does Your Business Need Enterprise Application …
Integrating Application Security Solutions with Enterprise Systems
In real enterprise environments, applications are always connected to something else—login systems, databases, cloud tools, mobile apps, or third-party platforms. That’s why security integration isn’t just about adding another tool. It’s about making sure security fits naturally into the systems teams already depend on, without slowing anyone down.
What smooth security integration looks like in practice
- Work with what’s already there
The best security solutions plug into existing systems like identity management, CRM, ERP, and cloud platforms. If security forces are forced to change everything overnight, it usually gets bypassed. - Keep access rules consistent everywhere
Using one centralized identity and access system helps avoid confusion. People shouldn’t have different permissions for every app—they should have one clear, controlled access experience. - Pay attention to the connections, not just the apps
A lot of security issues happen where systems talk to each other. Securing APIs, data flows, and third-party integrations is just as important as securing the application itself. - Don’t treat mobile apps as an exception
Mobile apps should follow the same security rules as core enterprise systems. This keeps enterprise application integration security consistent across web, mobile, and backend platforms. - Let automation do the heavy lifting
Integrating security checks into existing DevOps and monitoring tools reduces manual effort and helps teams catch issues early—without extra meetings or checklists. - Make security visible, not noisy
Centralized logs and alerts give security teams clarity without overwhelming developers or operations teams with constant warnings.
When application security solutions blend naturally into enterprise systems, security stops feeling like a blocker. Instead, it becomes part of how the organization works, quietly protecting data, users, and integrations while enabling collaboration and scale.
Conclusion
Creating secure enterprise applications is not about adopting every new security tool available, but about making intelligent, well-planned decisions from the start. By integrating security into application strategy, mobile experiences, and system integrations, enterprises can reduce risk while continuing to innovate and collaborate effectively.
A security-led approach enables businesses to protect valuable data, manage open-source and integration risks, and support modern workflows across web and mobile platforms. Many organizations also choose to work with a trusted Cybersecurity Service Provider to strengthen governance, risk management, and ongoing threat monitoring across enterprise environments.
Ultimately, secure enterprise apps uphold more than just security standards they are more stable, easier to manage, and better prepared for future growth and evolving digital threats.


 Healthcare App Development Services
Healthcare App Development Services
 Real Estate Web Development Services
Real Estate Web Development Services
 E-Commerce App Development Services
E-Commerce App Development Services E-Commerce Web Development Services
E-Commerce Web Development Services Blockchain E-commerce Development Company
Blockchain E-commerce Development Company
 Fintech App Development Services
Fintech App Development Services Fintech Web Development
Fintech Web Development Blockchain Fintech Development Company
Blockchain Fintech Development Company
 E-Learning App Development Services
E-Learning App Development Services
 Restaurant App Development Company
Restaurant App Development Company
 Mobile Game Development Company
Mobile Game Development Company
 Travel App Development Company
Travel App Development Company
 Automotive Web Design
Automotive Web Design
 AI Traffic Management System
AI Traffic Management System
 AI Inventory Management Software
AI Inventory Management Software
 AI Software Development
AI Software Development  AI Development Company
AI Development Company  AI App Development Services
AI App Development Services  ChatGPT integration services
ChatGPT integration services  AI Integration Services
AI Integration Services  Generative AI Development Services
Generative AI Development Services  Natural Language Processing Company
Natural Language Processing Company Machine Learning Development
Machine Learning Development  Machine learning consulting services
Machine learning consulting services  Blockchain Development
Blockchain Development  Blockchain Software Development
Blockchain Software Development  Smart Contract Development Company
Smart Contract Development Company  NFT Marketplace Development Services
NFT Marketplace Development Services  Asset Tokenization Company
Asset Tokenization Company DeFi Wallet Development Company
DeFi Wallet Development Company Mobile App Development
Mobile App Development  IOS App Development
IOS App Development  Android App Development
Android App Development  Cross-Platform App Development
Cross-Platform App Development  Augmented Reality (AR) App Development
Augmented Reality (AR) App Development  Virtual Reality (VR) App Development
Virtual Reality (VR) App Development  Web App Development
Web App Development  SaaS App Development
SaaS App Development Flutter
Flutter  React Native
React Native  Swift (IOS)
Swift (IOS)  Kotlin (Android)
Kotlin (Android)  Mean Stack Development
Mean Stack Development  AngularJS Development
AngularJS Development  MongoDB Development
MongoDB Development  Nodejs Development
Nodejs Development  Database Development
Database Development Ruby on Rails Development
Ruby on Rails Development Expressjs Development
Expressjs Development  Full Stack Development
Full Stack Development  Web Development Services
Web Development Services  Laravel Development
Laravel Development  LAMP Development
LAMP Development  Custom PHP Development
Custom PHP Development  .Net Development
.Net Development  User Experience Design Services
User Experience Design Services  User Interface Design Services
User Interface Design Services  Automated Testing
Automated Testing  Manual Testing
Manual Testing  Digital Marketing Services
Digital Marketing Services 
 Ride-Sharing And Taxi Services
Ride-Sharing And Taxi Services Food Delivery Services
Food Delivery Services Grocery Delivery Services
Grocery Delivery Services Transportation And Logistics
Transportation And Logistics Car Wash App
Car Wash App Home Services App
Home Services App ERP Development Services
ERP Development Services CMS Development Services
CMS Development Services LMS Development
LMS Development CRM Development
CRM Development DevOps Development Services
DevOps Development Services AI Business Solutions
AI Business Solutions AI Cloud Solutions
AI Cloud Solutions AI Chatbot Development
AI Chatbot Development API Development
API Development Blockchain Product Development
Blockchain Product Development Cryptocurrency Wallet Development
Cryptocurrency Wallet Development About Talentelgia
About Talentelgia  Our Team
Our Team  Our Culture
Our Culture 
 Healthcare App Development Services
Healthcare App Development Services Real Estate Web Development Services
Real Estate Web Development Services E-Commerce App Development Services
E-Commerce App Development Services E-Commerce Web Development Services
E-Commerce Web Development Services Blockchain E-commerce
Development Company
Blockchain E-commerce
Development Company Fintech App Development Services
Fintech App Development Services Finance Web Development
Finance Web Development Blockchain Fintech
Development Company
Blockchain Fintech
Development Company E-Learning App Development Services
E-Learning App Development Services Restaurant App Development Company
Restaurant App Development Company Mobile Game Development Company
Mobile Game Development Company Travel App Development Company
Travel App Development Company Automotive Web Design
Automotive Web Design AI Traffic Management System
AI Traffic Management System AI Inventory Management Software
AI Inventory Management Software AI Software Development
AI Software Development AI Development Company
AI Development Company ChatGPT integration services
ChatGPT integration services AI Integration Services
AI Integration Services Machine Learning Development
Machine Learning Development Machine learning consulting services
Machine learning consulting services Blockchain Development
Blockchain Development Blockchain Software Development
Blockchain Software Development Smart contract development company
Smart contract development company NFT marketplace development services
NFT marketplace development services IOS App Development
IOS App Development Android App Development
Android App Development Cross-Platform App Development
Cross-Platform App Development Augmented Reality (AR) App
Development
Augmented Reality (AR) App
Development Virtual Reality (VR) App Development
Virtual Reality (VR) App Development Web App Development
Web App Development Flutter
Flutter React
Native
React
Native Swift
(IOS)
Swift
(IOS) Kotlin (Android)
Kotlin (Android) MEAN Stack Development
MEAN Stack Development AngularJS Development
AngularJS Development MongoDB Development
MongoDB Development Nodejs Development
Nodejs Development Database development services
Database development services Ruby on Rails Development services
Ruby on Rails Development services Expressjs Development
Expressjs Development Full Stack Development
Full Stack Development Web Development Services
Web Development Services Laravel Development
Laravel Development LAMP
Development
LAMP
Development Custom PHP Development
Custom PHP Development User Experience Design Services
User Experience Design Services User Interface Design Services
User Interface Design Services Automated Testing
Automated Testing Manual
Testing
Manual
Testing About Talentelgia
About Talentelgia Our Team
Our Team Our Culture
Our Culture
















 Write us on:
Write us on:  Business queries:
Business queries:  HR:
HR: