The practice of outsourcing to third-party software development teams has become a business strategy to control their expenses, connect with highly skilled labor worldwide, and grow teams quickly. The cost-cutting measures can, however, cause new problems with security. The greater the access vendors are given to the systems, the greater the chances of cyberattacks, data leaks, or errors occurring. As the dependency on cybersecurity for outsourced software teams grows, so does the necessity for stronger protective measures to guard confidential information.
For businesses to mitigate the threat posed by the outsourcing of critical elements of their tech infrastructure, they must incorporate the most efficient data security systems available. As per Gartner research, the global security market was $183 billion in 2024, which is projected to reach $292 billion by 2028 with a CAGR of 12.5% during the forecast period. There are several good reasons for these huge numbers. This widespread practice of outsourcing cybersecurity for remote development teams will improve data security and operational efficiency.
Understanding Cybersecurity As a Service: Challenges & Benefits
Numerous services provide functional featuresthat have been simplified, either by eliminating some complexities or by streamlining certain workflows, like with Software-as-a-Service (SaaS), where the software is hosted on a cloud, and users pay a subscription to access it. The same principle applies in Cybersecurity— it’s termed as ‘cybersecurity as a service’. There are several ways to secure applications, and multiple businesses are relying on outsourcing some of their security requirements to cybersecurity as service providers to improve and manage their security and overall cybersecurity infrastructure.

What Is Cybersecurity Outsourcing?
Cybersecurity outsourcing is the practice of handing some or all of your security responsibilities to external specialists rather than trying to build and maintain everything in‑house. Instead of hiring a full team of security engineers, analysts, and compliance experts, an enterprise pays a third‑party provider to monitor threats, harden systems, and respond to incidents on its behalf.
The frameworks mentioned below act like a shared language between you and your security partners, so expectations are clear and measurable.
- Cyber Assessment Framework (CAF): Assesses resilience across risk management, data protection, and incident response—ideal for holistic vendor audits.
- Cyber Essentials: Baseline hygiene standard covering firewalls, access control, malware protection, and patching to block common attacks.
- IASME Governance: Practical governance for SMB vendors—risk management, data protection, and continuity without enterprise complexity.
- SOC 2: Audits trust services (security, availability, confidentiality) over time, proving mature controls for strategic partners.
- ISO Standards:
- ISO 27001: Information security management system (ISMS) for systematic risk treatment.
- ISO 22301: Business continuity to ensure development continues during disruptions.
- PCI-DSS: Strict payment data controls—hardened networks, logging, testing—for teams touching cardholder information.
- Choose by risk: Cyber Essentials for low-risk vendors, SOC 2/ISO for core partners holding sensitive code
What are The Cybersecurity Challenges That Businesses Face?
Distributed teams sound great until you realize cybersecurity is now a 24/7 global game of whack‑a‑mole. Here are the brutal realities enterprises battle daily:
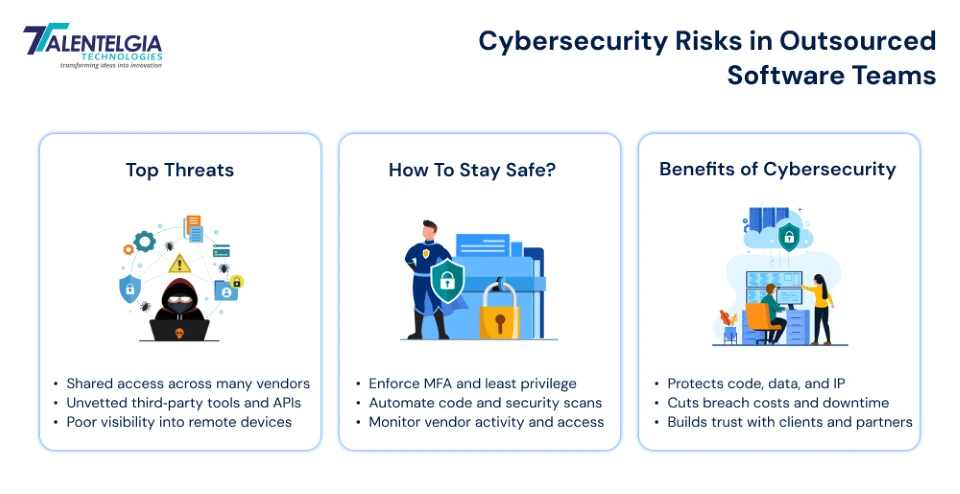
- Vendor concentration risk: Too many eggs in one basket—when a major cloud provider or dev tool gets hit, your entire ecosystem goes down. 2025 saw third‑party incidents spike 27%, with tech services hardest hit.
- Third‑party access chaos: 48% of orgs now see remote vendor access as their weakest link, with over half experiencing breaches from contractors last year. Limited oversight means forgotten accounts and over‑privileges linger.
- Cloud misconfigs and sprawl: Rapid cloud adoption outpaces security—public S3 buckets, weak IAM, exposed APIs. Recovery from these can double costs to $1.2B+ for small firms alone.
- Human error in distributed setups: Remote workers on public WiFi, weak passwords (25% of breaches), and phishing clicks (38% of incidents) create constant openings that attackers exploit at scale.
- Resource and visibility gaps: No budget/expertise for full monitoring across vendors, plus high turnover means new risks daily. Two‑thirds expect vendor breaches to rise further.
Why Cybersecurity Is Important for Outsourced & Remote Software Teams?
Working from home offers a number of advantages, such as no daily travel, more flexibility, and improved balance between work and personal life. However, it does also pose its own risks. Employees working remotely may use personal devices, connect to Wi-Fi that is not protected (or is public, like in coffee shops, or co-working spaces). All of this makes it easier for cybercriminals to execute their attacks, like hacking, phishing, and data theft.
Remote teams need to understand risks when it comes to business data, especially sensitive data. Customer data, financial information, and proprietary business plans all come with risks that need to be safeguarded with robust cybersecurity. Here are some tips to help keep it safe!
- Protects sensitive data and IP across borders: Outsourced projects routinely involve sharing source code, architecture documents, test data, and sometimes real customer information; a single breach can cost millions and permanently damage trust. Robust controls (access management, encryption, secure SDLC) let you tap global talent without handing attackers your product roadmap.
- Reduces third‑party breach exposure: Around one‑third of global data breaches now originate from third parties, and nearly half of those hit technology products and services. Investing in cybersecurity for vendors—through standards, monitoring, and contracts—directly lowers the odds that a weak link in your extended team becomes tomorrow’s headline incident.
- Keeps remote work productive instead of risky: Secured remote setups (cloud security, centralized management, real‑time monitoring) let teams collaborate from anywhere without constant fear of leaks or ransomware. When people trust their tools and connections, they focus on shipping features instead of fighting fires.
- Ensures compliance follows the work, not the office: Regulations like GDPR and industry rules still apply when development is done offshore or from home offices, and fines don’t care whose laptop leaked the data. A solid cybersecurity baseline for outsourced teams helps prove due diligence to regulators, auditors, customers, and boards.
- Builds long‑term, high‑trust partnerships: Vendors that align with your security expectations—policies, audits, incident playbooks—become strategic partners rather than disposable suppliers. Over time, shared security practices mean faster onboarding, smoother projects, and far less friction every time a new team, region, or product goes live.
Why Cybersecurity Risks are Growing In the Tech Industry?
Cybersecurity risk in tech isn’t just “getting worse”—it’s snowballing. More code, more tools, more data, more vendors, and the same 24 hours in a day. That gap is where attackers live.
- Shared access across many teams: Multiple in‑house, outsourced, and remote teams often share access to the same code, cloud resources, and data, so one compromised account or careless user can expose everything.
- Different security postures and standards: Each vendor or team follows its own practices, tools, and policies, creating uneven protection and making it hard to enforce a consistent security baseline.
- Heavy reliance on third‑party tools: From CI/CD platforms to chat apps and cloud services, every extra tool becomes another potential entry point, misconfiguration risk, or place where sensitive data can leak.
- Weak oversight and visibility: Security and IT teams rarely have full, real‑time visibility into what remote and outsourced teams are doing—what they install, which data they copy, or which services they expose.
- Rising automation and attacker sophistication: Attackers now use automation and AI to scan for exposed keys, misconfigured APIs, and vulnerable services at scale, so even small mistakes by distributed teams are found and exploited quickly.
Things You Must Know Before Choosing a Cybersecurity Partner For Your Business
Choosing a cybersecurity partner is crucial for your business’s safety and compliance. Clients often report that one of the main reasons they change their cybersecurity partners is poor communication. Working with a new cybersecurity partner can be difficult, especially when your previous experiences have been unfavourable. So, to assist you in finding the best cybersecurity partner for your business, we have prepared the following checklist:
- Real-world Defence Experience: Skip generic case studies. Demand proof they’ve protected GitHub Enterprise, CI/CD pipelines, and offshore vendor access specifically. Experience securing Codespaces, Gitpod, or Jenkins runners matters more than generic cloud certs.
- 24/7 SOC Coverage That Matches Your Timezones: Your Indian devs log off as Eastern Europe wakes up. Can their SOC analysts handle midnight alerts across your vendor footprint? Ask for shift handoff SLAs and language coverage for global incident response.
- Native Integrations with Your Tools: They must plug directly into GitHub Actions, Jira workflows, Slack channels, and your cloud IAM (AWS IAM Roles Anywhere, Azure AD). No “we’ll build a custom connector later” excuses—test API connectivity during demos.
- Transparent Breach History & Response Proof: Ask for their own SOC 2 Type II report (not just a logo) and anonymised IR case studies. How fast did they contain their last breach? What was the forensic post-mortem? Honest partners share scars, not just trophies.
- Vendor Management Expertise: They should have pre-built vendor risk scoring, offshore team monitoring templates, and compliance mapping for SOC 2, ISO 27001, and DPDP Act. Bonus if they offer “vendor security scorecards” you can forward to your CISO.
- Scalable Pricing: Fixed per-endpoint pricing kills you when vendor headcount doubles. Look for tiered models (Core SOC → Advanced Hunting → Full IR Retainer) with clear expansion costs and no “surprise engineering fees.”
Conclusion
Cybersecurity is an adaptable, convenient and cost-friendly method for enterprises to establish their security defenses for outsourced development teams. Enterprises usually go for CSaaS providers under selective criteria and give them the freedom to change, grow, and modify cybersecurity solutions.|
When it comes to requirements for a particular IT company, there are numerous possible solutions and cybersecurity providers to assist them. Every search for cybersecurity must begin with ian n-depth analysis of the software development team's needs before looking for a reliable vendor. This way of finding a cybersecurity partner becomes easy and helps to establish a long-term relationship that promotes growth and success.


 Healthcare App Development Services
Healthcare App Development Services
 Real Estate Web Development Services
Real Estate Web Development Services
 E-Commerce App Development Services
E-Commerce App Development Services E-Commerce Web Development Services
E-Commerce Web Development Services Blockchain E-commerce Development Company
Blockchain E-commerce Development Company
 Fintech App Development Services
Fintech App Development Services Fintech Web Development
Fintech Web Development Blockchain Fintech Development Company
Blockchain Fintech Development Company
 E-Learning App Development Services
E-Learning App Development Services
 Restaurant App Development Company
Restaurant App Development Company
 Mobile Game Development Company
Mobile Game Development Company
 Travel App Development Company
Travel App Development Company
 Automotive Web Design
Automotive Web Design
 AI Traffic Management System
AI Traffic Management System
 AI Inventory Management Software
AI Inventory Management Software
 AI Software Development
AI Software Development  AI Development Company
AI Development Company  AI App Development Services
AI App Development Services  ChatGPT integration services
ChatGPT integration services  AI Integration Services
AI Integration Services  Generative AI Development Services
Generative AI Development Services  Natural Language Processing Company
Natural Language Processing Company Machine Learning Development
Machine Learning Development  Machine learning consulting services
Machine learning consulting services  Blockchain Development
Blockchain Development  Blockchain Software Development
Blockchain Software Development  Smart Contract Development Company
Smart Contract Development Company  NFT Marketplace Development Services
NFT Marketplace Development Services  Asset Tokenization Company
Asset Tokenization Company DeFi Wallet Development Company
DeFi Wallet Development Company Mobile App Development
Mobile App Development  IOS App Development
IOS App Development  Android App Development
Android App Development  Cross-Platform App Development
Cross-Platform App Development  Augmented Reality (AR) App Development
Augmented Reality (AR) App Development  Virtual Reality (VR) App Development
Virtual Reality (VR) App Development  Web App Development
Web App Development  SaaS App Development
SaaS App Development Flutter
Flutter  React Native
React Native  Swift (IOS)
Swift (IOS)  Kotlin (Android)
Kotlin (Android)  Mean Stack Development
Mean Stack Development  AngularJS Development
AngularJS Development  MongoDB Development
MongoDB Development  Nodejs Development
Nodejs Development  Database Development
Database Development Ruby on Rails Development
Ruby on Rails Development Expressjs Development
Expressjs Development  Full Stack Development
Full Stack Development  Web Development Services
Web Development Services  Laravel Development
Laravel Development  LAMP Development
LAMP Development  Custom PHP Development
Custom PHP Development  .Net Development
.Net Development  User Experience Design Services
User Experience Design Services  User Interface Design Services
User Interface Design Services  Automated Testing
Automated Testing  Manual Testing
Manual Testing  Digital Marketing Services
Digital Marketing Services 
 Ride-Sharing And Taxi Services
Ride-Sharing And Taxi Services Food Delivery Services
Food Delivery Services Grocery Delivery Services
Grocery Delivery Services Transportation And Logistics
Transportation And Logistics Car Wash App
Car Wash App Home Services App
Home Services App ERP Development Services
ERP Development Services CMS Development Services
CMS Development Services LMS Development
LMS Development CRM Development
CRM Development DevOps Development Services
DevOps Development Services AI Business Solutions
AI Business Solutions AI Cloud Solutions
AI Cloud Solutions AI Chatbot Development
AI Chatbot Development API Development
API Development Blockchain Product Development
Blockchain Product Development Cryptocurrency Wallet Development
Cryptocurrency Wallet Development About Talentelgia
About Talentelgia  Our Team
Our Team  Our Culture
Our Culture 
 Healthcare App Development Services
Healthcare App Development Services Real Estate Web Development Services
Real Estate Web Development Services E-Commerce App Development Services
E-Commerce App Development Services E-Commerce Web Development Services
E-Commerce Web Development Services Blockchain E-commerce
Development Company
Blockchain E-commerce
Development Company Fintech App Development Services
Fintech App Development Services Finance Web Development
Finance Web Development Blockchain Fintech
Development Company
Blockchain Fintech
Development Company E-Learning App Development Services
E-Learning App Development Services Restaurant App Development Company
Restaurant App Development Company Mobile Game Development Company
Mobile Game Development Company Travel App Development Company
Travel App Development Company Automotive Web Design
Automotive Web Design AI Traffic Management System
AI Traffic Management System AI Inventory Management Software
AI Inventory Management Software AI Software Development
AI Software Development AI Development Company
AI Development Company ChatGPT integration services
ChatGPT integration services AI Integration Services
AI Integration Services Machine Learning Development
Machine Learning Development Machine learning consulting services
Machine learning consulting services Blockchain Development
Blockchain Development Blockchain Software Development
Blockchain Software Development Smart contract development company
Smart contract development company NFT marketplace development services
NFT marketplace development services IOS App Development
IOS App Development Android App Development
Android App Development Cross-Platform App Development
Cross-Platform App Development Augmented Reality (AR) App
Development
Augmented Reality (AR) App
Development Virtual Reality (VR) App Development
Virtual Reality (VR) App Development Web App Development
Web App Development Flutter
Flutter React
Native
React
Native Swift
(IOS)
Swift
(IOS) Kotlin (Android)
Kotlin (Android) MEAN Stack Development
MEAN Stack Development AngularJS Development
AngularJS Development MongoDB Development
MongoDB Development Nodejs Development
Nodejs Development Database development services
Database development services Ruby on Rails Development services
Ruby on Rails Development services Expressjs Development
Expressjs Development Full Stack Development
Full Stack Development Web Development Services
Web Development Services Laravel Development
Laravel Development LAMP
Development
LAMP
Development Custom PHP Development
Custom PHP Development User Experience Design Services
User Experience Design Services User Interface Design Services
User Interface Design Services Automated Testing
Automated Testing Manual
Testing
Manual
Testing About Talentelgia
About Talentelgia Our Team
Our Team Our Culture
Our Culture


















 Write us on:
Write us on:  Business queries:
Business queries:  HR:
HR: